Brute Forcing
Burp
So, fire up the burp suite. Set the proxy in your firefox to use burp as a proxy. You can also use the foxy proxy addon to set the burp proxy.
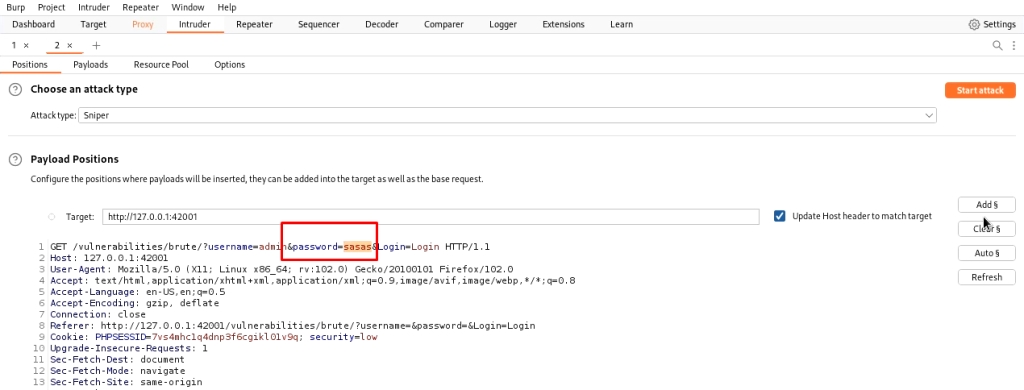
Now go to the burp proxy tab, and set it to intercept the requests. Submit a request from firefox to log in with the wrong credentials. the complete request will be shown in the burp. Now right-click on it and send it to the intruder module.
In the intruder tab, clear all targets and locate the password field and add it as a target. Now in the payloads tab, you can set the wordlist. I am using john.lst.
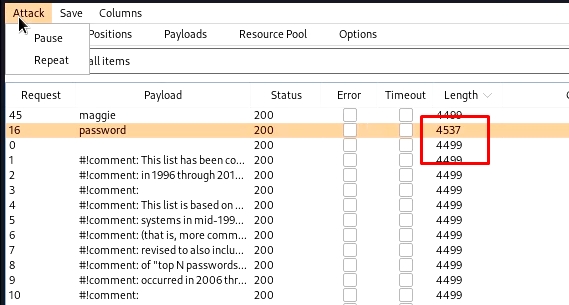
Now start the attack, burp will try to brute force it. Keep looking for the response size. The request/ response with a changed response size will be our matched password.
Hydra
Hydra is a password-cracking tool that is available as part of the Kali Linux distribution of security tools. It is a network login cracking tool that is used to perform brute-force attacks on network protocols, such as HTTP, FTP, Telnet, and SSH.
Hydra is designed to be fast and efficient, and it can perform parallel attacks on multiple targets at the same time. It has a large number of modules that can be used to attack different protocols and services, and it can be used to crack passwords for a variety of different systems and applications.
Hydra is a powerful tool that can be used by security professionals and ethical hackers to test the security of networks and systems, as well as by malicious actors to try to gain unauthorized access to systems and data
Hydra can brute force the password much faster than the burp suite community edition. However, you need to format the command for it.
You need to provide it complete URL of the form. You can get it from the network tab if you inspect a page. Replace username and password with ^USER^ and ^PASS^ respectively.
Get the cookie information from the Storage tab in debug menu.
Set the login failure information with the F flag
Now start the attack with the following command and hydra will brute force the password.

Hydra POST Form bruteforcing
Analyzed login form structure via page source.
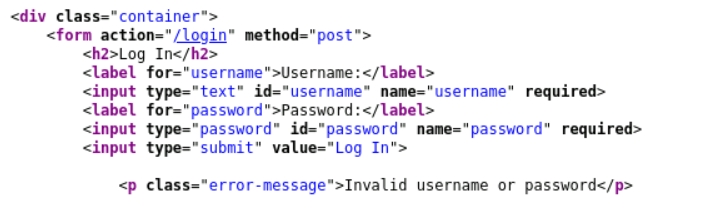
Used Hydra to brute-force login credentials.
-L specifies a username list
-P specifies a password list.
target.ine.local is the target website.
http-post-form "/login:username=^USER^&password=^PASS^:Invalid username or password" Attempts login with username-password pairs.
Detects failed attempts by matching "Invalid username or password".
Hydra Get form bruteforcing
FFUF
Capture the request in burp and then change the password field

Now, use the following command

Now you can filter out on size

And we have our results

Fuzzing username and pass

Then we need to set the attack as clusterbomb

Last updated